Key encapsulation mechanism
Imagine you have a secret toy, but you can't just give it to your friend directly because it's too precious. So, you put the toy inside a special box and make sure no one can see what's inside it. Then, you lock the box with a key and give the key to your friend.
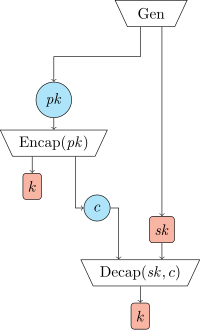
Similarly, in the world of cybersecurity, we have sensitive information that we want to keep safe but we can't just give it to anyone. So, we use a key encapsulation mechanism (KEM) to protect our data.
KEM is a way of using two types of keys: a secret key and a public key. The secret key is like the key to the box that holds your secret toy. You keep this secret key to yourself and use it to unlock the box whenever you need to access your toy.
Meanwhile, the public key is like a copy of the key to the box that you give to your friend. With this public key, your friend can encrypt messages and send them to you securely. The encrypted message can only be decrypted using your secret key, which only you have.
So, in summary, KEM is a way of keeping sensitive information safe by using two keys: a secret key and a public key. These keys work together to ensure that only the intended recipient can access the information. Think of it like a special box with a key that only certain people can unlock.
Similarly, in the world of cybersecurity, we have sensitive information that we want to keep safe but we can't just give it to anyone. So, we use a key encapsulation mechanism (KEM) to protect our data.
KEM is a way of using two types of keys: a secret key and a public key. The secret key is like the key to the box that holds your secret toy. You keep this secret key to yourself and use it to unlock the box whenever you need to access your toy.
Meanwhile, the public key is like a copy of the key to the box that you give to your friend. With this public key, your friend can encrypt messages and send them to you securely. The encrypted message can only be decrypted using your secret key, which only you have.
So, in summary, KEM is a way of keeping sensitive information safe by using two keys: a secret key and a public key. These keys work together to ensure that only the intended recipient can access the information. Think of it like a special box with a key that only certain people can unlock.
Related topics others have asked about:
