ARP spoofing
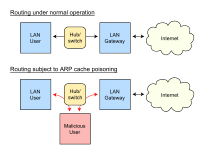
Imagine you're in a big playground with lots of kids playing. Each kid has their own name tag that tells everyone their name and which toy they're playing with. This helps you know who's who and avoid taking someone else's toy by mistake.
Now, imagine a bully comes along and takes some of the name tags. They start switching the names and toys around so that it gets really confusing. You might go to play with your friend Sally, but when you get there, Sally's name tag says "Bob" and she's actually playing with a different toy, so you get confused and frustrated.
This is kind of like what happens with ARP spoofing. In computer networks, each device has a unique address, like a name tag, called a MAC address. This helps devices communicate with each other and know who's who. But a hacker can use a tool called ARP spoofing to trick devices into thinking they're someone else by changing their MAC address.
So just like the bully switching name tags, the hacker can switch MAC addresses around and make it hard for devices to communicate with each other properly. This can let them intercept data, steal sensitive information, or even launch a full-blown attack on the network.
To prevent ARP spoofing, security measures like implementing VLANs, using MAC filtering, or using encryption like SSL/TLS can be used. Just like the playground rules, it's important for everyone in the network to be able to trust each other's "name tags" and toys so they can play together safely and securely.
Now, imagine a bully comes along and takes some of the name tags. They start switching the names and toys around so that it gets really confusing. You might go to play with your friend Sally, but when you get there, Sally's name tag says "Bob" and she's actually playing with a different toy, so you get confused and frustrated.
This is kind of like what happens with ARP spoofing. In computer networks, each device has a unique address, like a name tag, called a MAC address. This helps devices communicate with each other and know who's who. But a hacker can use a tool called ARP spoofing to trick devices into thinking they're someone else by changing their MAC address.
So just like the bully switching name tags, the hacker can switch MAC addresses around and make it hard for devices to communicate with each other properly. This can let them intercept data, steal sensitive information, or even launch a full-blown attack on the network.
To prevent ARP spoofing, security measures like implementing VLANs, using MAC filtering, or using encryption like SSL/TLS can be used. Just like the playground rules, it's important for everyone in the network to be able to trust each other's "name tags" and toys so they can play together safely and securely.
Related topics others have asked about:
